Android/Obad.A is mobile malware that has been described as very
complex. Truly it is one of the most complex we’ve seen because it:
- Uses Bluetooth to infect other Android devices
- Accepts commands from the attacker
- Hides from the Device Administration list
This is a good collection of malicious activities for a modern piece of
malware. Is it unique, though? No, other mobile malware has propagated via
Bluetooth, as early as SymbOS/Cabir. Earlier mobile botnets on Symbian,
Windows Mobile, and even Android have also accepted commands from attackers’
control servers. That last item, though, disappearing from a standard
listing makes Android/Obad a bit more insidious.
Hidden apps: unwelcome guests?
If you can’t find it, you can’t remove it. Nearly every other piece of
Android malware that doesn’t have root access can be found and discovered.
Android/Obad uses a vulnerability that keeps it off the standard
Device Administration list. The vulnerability isn’t yet closed, so it’s very
likely we’ll see other malware authors start to exploit it.
Peek-a-boo, I see you
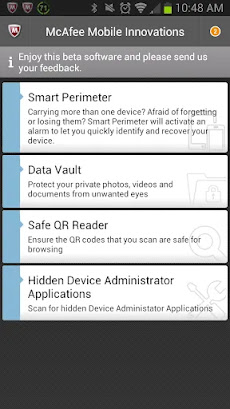
Fortunately, we have added hidden-app detection capabilities to the latest
edition of our McAfee Mobile Innovations app (MMI). The MMI app hosts a
bunch of our other new beta features as well. Protecting private data (Data
Vault), letting your devices warn you before you lose them (Smart
Perimeter), and a tool to avoid dangerous QR codes (Safe QR Reader).
|
|
Select “Hidden Device Administrator Applications” from McAfee Mobile Innovations menu. |
The Hidden Device Administrator Detector searches and finds all apps that have
Device Admin access, even if they’re using the vulnerability to hide from the
Android OS. Once you run it, it will give you a list of all hidden Device
Admin apps and the option to deactivate or remove them.
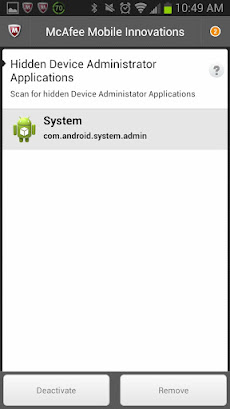 |
| A list of all detected Administrator Apps. |
Malware attempting to hide via vulnerabilities face a short life. As soon as software publishers fix the bugs in their software or antimalware apps add detection and removal, their time is up.

No comments:
Post a Comment